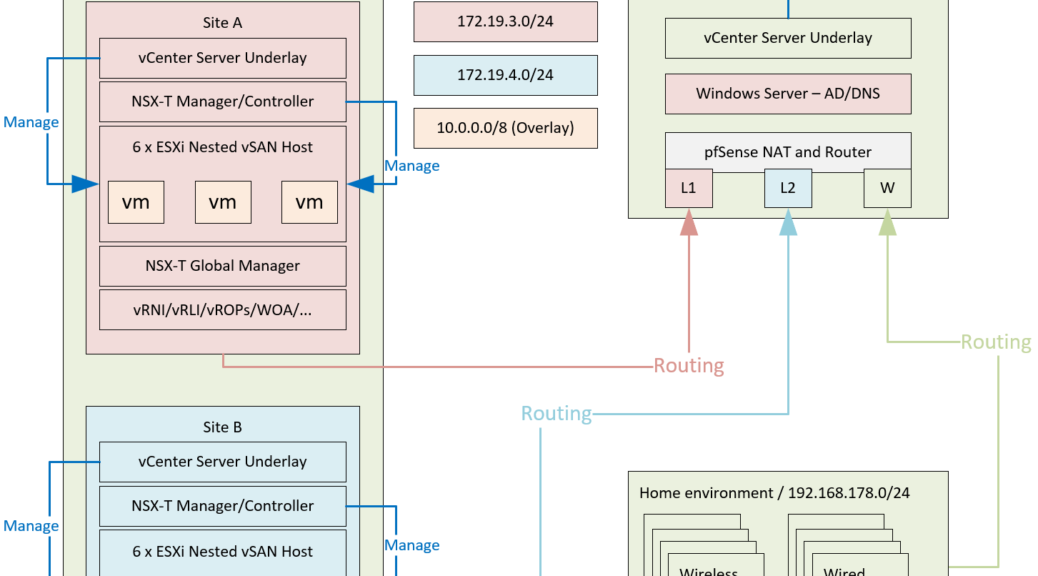
NSX-T 3.0 – Initial Configuration
This blog is to describe the initial configuration of NSX-T 3.0. After deploying the appliances and combining them into one environment (https://my-sddc.net/nsx-t-global-manager-installation-and-initial-setup/) and deploying the vSphere/vSAN environment (https://my-sddc.net/building-the-lab-vsphere-and-vsan/) it is time to combine the two and create the virtual network environment. As a reminder, our environment is going to look like this: but that’s mainly the physical side of it. The virtual side is still something I have to figure out, but for now, it’s roughly going to look like…